2024"磐石行动"演练 Writeup
四象限守护者队 reverse 部分 WP
“磐石行动”2024第二届全国高校网络安全攻防活动:CTF 个人排名15,团体排名17,总排35进入复赛。出了三道 re ,最简单的签到没做出来有点可惜了,这是我距离 ak 最近的一次了。然后就是学到了很多新的东西比如说固件逆向,虽然说有点公式化了但是还是蛮有难度的(好在加密都比较简单)。然后比较可惜的是数据安全通道一题未出,真会不了一点,太吃脑子了。


ezlogin
简单des加密藏得很深,混淆的函数太多了有点难找,重点是找到key。这个软件不能debug权限不够,那就解包加权限,然后调试出key=’key_here’
1、先反编译apk文件,删除原来的apk文件
1 | apktool d ezlogin.APK |
2、给AndroidManifest.xml设置为debuggable
1 | android:debuggable="true" |
3、重新打包
1 | apktool b ezlogin |
4、在dist文件夹找到新的apk,对文件进行对齐
1 | zipalign -p -f -v 4 ezlogin.apk ezlogin1.apk |
5、进行重新签名
1 | apksigner sign --ks abc.keystore ezlogin1.apk |
1 | import base64 |
easy_iot
第一次做固件逆向题完全没有思路,参考这篇文章
1 | binwalk -e out.bin |
用binwalk把固件分离出来,然后他说flag在最简单的文件里面我直接找bin然后是文件修改时间最晚的就只有bash,套了一层upx的壳,去掉然后放进ida反编译
1 | a=[5, 15, 2, 4, 24, 54, 85, 47, 85, 39, 86, 85, 85, 34, 86, 58, 81, 53, 86, 86, 18, 38, 86, 57, 22,85, 86, 47, 22, 81, 85, 58, 32, 36, 86, 57, 32, 30] |
easystm32
第一次操作这种固件,参考文章:
【MCU】可怕,别人把我MCU固件给反汇编了!(逆向)-CSDN博客



按c反编译之后查看string可以发现提示是:
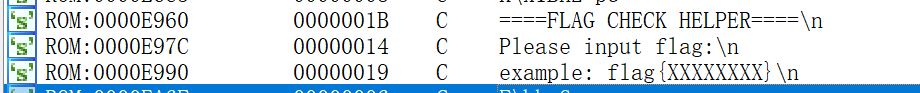
随后搜索有可能加密后的字符串:

加密方法:

解码就完事:
1 | a=[0x66,0x6D,0x63,0x64,0x7f,0x57,0x37,0x4b,0x3c,0x7b,0x58,0x40,0x3a,0x70] |
再转成md5
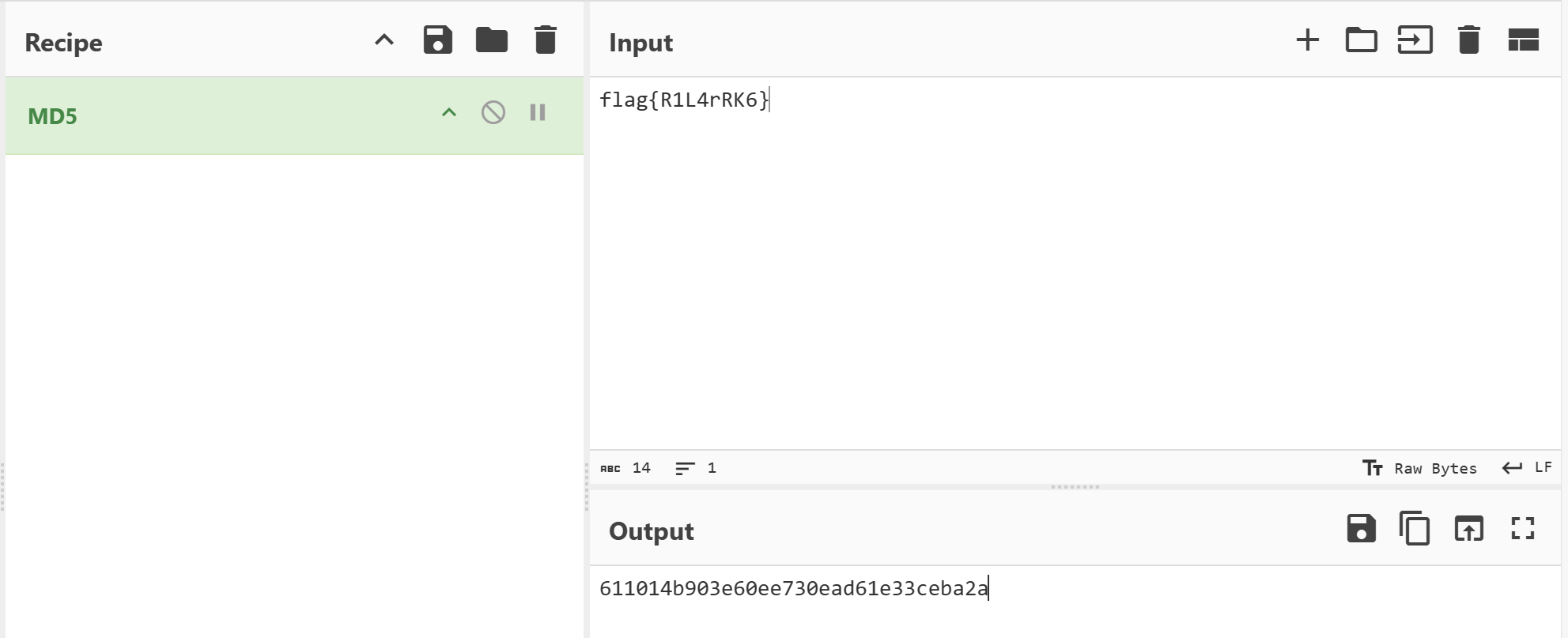
今天天气怎么样
第一部分包含两个函数一加密一比较:crazy()、ohh()
1 | //crazy() |
1 |
|
然后发现后面还有一关,要调用my_function(),但是都是花指令和奇怪的跳转,打断点单步调试再create function就找到了实际调用逻辑。
1 | puts("please input your True flag:"); |
单步调试得到s盒和最后要比对的值,rc4求解即可得出答案
1 | a=[48, 114, 153, 160, 71, 163, 108, 200, 150, 187, 78, 151, 90, 7, 167, 38, 120, 18, 132, 216, 144, 9, 210, 249, 62, 52, 64, 73, 109, 29, 66, 125, 175, 119, 208, 47, 193, 138, 21, 159, 87, 241, 40, 218, 92, 234, 59, 91, 180, 99, 243, 121, 248, 148, 2, 55, 95, 220, 183, 178, 82, 0, 98, 12, 69, 36, 17, 237, 252, 165, 14, 31, 68, 113, 8, 254, 67, 37, 65, 177, 105, 42, 227, 129, 93, 209, 219, 147, 251, 10, 83, 238, 225, 70, 28, 253, 168, 236, 101, 89, 61, 201, 33, 191, 217, 128, 136, 23, 211, 231, 247, 145, 146, 112, 6, 80, 184, 197, 239, 255, 43, 134, 111, 97, 57, 81, 103, 11, 106, 172, 26, 1, 39, 226, 230, 215, 158, 53, 244, 50, 224, 35, 4, 152, 72, 164, 115, 58, 161, 126, 100, 117, 154, 46, 174, 79, 223, 214, 137, 186, 5, 24, 190, 22, 49, 235, 195, 162, 179, 60, 44, 203, 233, 245, 54, 74, 135, 156, 143, 204, 246, 140, 16, 124, 194, 171, 20, 88, 76, 181, 212, 77, 15, 188, 3, 166, 202, 142, 176, 30, 27, 206, 192, 213, 240, 221, 133, 189, 84, 96, 131, 110, 170, 141, 196, 222, 63, 242, 13, 45, 107, 155, 51, 198, 127, 94, 41, 34, 149, 205, 185, 182, 56, 250, 157, 139, 173, 123, 32, 232, 199, 116, 104, 75, 25, 122, 102, 207, 229, 118, 228, 169, 130, 19, 86, 85] |
All articles in this blog are licensed under CC BY-NC-SA 4.0 unless stating additionally.







